Unlock Remote Pi Power: SSH For IoT Devices
In today's interconnected world, the ability to manage and monitor devices remotely is no longer a luxury but a necessity, especially when dealing with Internet of Things (IoT) projects. For enthusiasts and professionals alike, the Raspberry Pi has emerged as a cornerstone in the IoT landscape, offering unparalleled versatility and a robust platform for innovation. However, harnessing its full potential often requires secure and efficient remote access, and this is where the powerful combination of SSH (Secure Shell) and a dedicated remote IoT platform truly shines.
This comprehensive guide will walk you through everything you need to know about setting up a remote IoT platform using SSH on a Raspberry Pi, empowering you to unlock the full potential of your Raspberry Pi for remote IoT projects. Whether you're a beginner taking your first steps into remote server management or an experienced developer looking to streamline your IoT ecosystem, this article is designed to provide clear, actionable insights into mastering secure remote access for your Pi projects.
Table of Contents
- Understanding SSH and Remote IoT
- The Raspberry Pi as an IoT Powerhouse
- The RemoteIoT Platform: A Game Changer for Raspberry Pi Users
- Enabling SSH on Your Raspberry Pi: A Step-by-Step Guide
- Mastering Remote Control and File Transfer
- Enhancing Security: Avoiding Pitfalls and Best Practices
- Revolutionizing IoT Projects with RemoteIoT Monitoring
- Overcoming NAT and Firewall Challenges with Secure Tunnels
- Conclusion: Mastering SSH RemoteIoT Raspberry Pi
Understanding SSH and Remote IoT
At its core, SSH, or Secure Socket Shell, is a network protocol that allows developers and users to connect to other computers by establishing a secure terminal session. It's the backbone of secure remote access, providing an encrypted connection over an unsecured network. In the context of IoT, where devices are often deployed in remote locations or behind restrictive networks, SSH becomes indispensable. It enables users to execute commands, transfer files, and manage their IoT devices as if they were physically connected to them. This capability is crucial for maintaining and monitoring IoT activity in real-time, ensuring safe and efficient operation, especially in business settings where continuous oversight is key. When we talk about a remote IoT platform, we're referring to a system that facilitates the management, monitoring, and control of IoT devices from a centralized location, typically through a web interface or a dedicated application. The integration of SSH into such a platform elevates its security and functionality, providing a robust conduit for interaction with edge devices like the Raspberry Pi. This synergy ensures that your data and commands are transmitted securely, protecting against unauthorized access and potential vulnerabilities. The concept of "ssh remoteiot raspberry pi free download" is revolutionizing how developers and hobbyists interact with IoT devices, making advanced remote management accessible to a broader audience.The Raspberry Pi as an IoT Powerhouse
The Raspberry Pi, a series of small single-board computers, has gained immense popularity in the IoT community due to its low cost, compact size, and powerful capabilities. It serves as an excellent platform for a myriad of IoT applications, from home automation systems to environmental monitoring sensors in remote locations. Its GPIO (General Purpose Input/Output) pins allow for easy integration with various sensors and actuators, making it a versatile choice for prototyping and deploying IoT solutions. For Raspberry Pi users, SSH offers a powerful way to control IoT devices remotely. Whether you’re managing a complex home automation system, collecting data from sensors in a remote agricultural field, or simply checking the status of your smart garden, SSH provides the secure conduit needed. The ability to remotely access your Pi means you don't need a physical display, keyboard, or mouse connected to it, which is incredibly convenient for headless setups and deployed devices. This flexibility makes the Raspberry Pi an ideal candidate for integration with remote IoT platforms, extending its reach and utility far beyond local network boundaries.The RemoteIoT Platform: A Game Changer for Raspberry Pi Users
The remote IoT platform stands out for its simplicity and versatility, making it an ideal choice for those who need to download and configure Raspberry Pi devices without the traditional complexities. It bridges the gap between your remote Raspberry Pi and your management interface, providing a secure and intuitive way to interact with your IoT ecosystem. One of the key advantages of using the remote IoT platform is the ability to download and configure SSH settings directly, streamlining what can often be a cumbersome manual process. This platform aims to simplify the entire lifecycle of remote IoT device management, from initial setup to ongoing monitoring and troubleshooting. In a world where security breaches are a constant threat, the remote IoT platform prioritizes secure communication. It leverages established protocols like SSH to ensure that all interactions with your Raspberry Pi are encrypted and authenticated. This focus on security means you can confidently manage your devices, knowing that your data is protected. The platform's design philosophy centers on providing a comprehensive yet user-friendly experience, making advanced remote capabilities accessible to a wider audience, regardless of their technical expertise. Discover how remote IoT monitoring SSH download Raspberry Pi can revolutionize your IoT projects by providing a robust, secure, and easy-to-use management solution.Seamless Configuration and Downloads
When we talk about "remote iot platform ssh raspberry pi download," we're essentially discussing how to download and configure the necessary software to enable SSH and integrate your Pi with the platform. The remote IoT platform simplifies this significantly. Instead of manually downloading SSH clients or configuring complex network settings, the platform often provides tools or scripts that automate this process. This includes the ability to download Raspberry Pi configurations without SSH initially, and then, once the platform's service is installed, to download and configure SSH settings securely through the platform's interface. This seamless approach saves time and reduces the potential for configuration errors, making it an ideal solution for deploying multiple devices. The platform's capability to manage configurations remotely is a powerful feature. It means you can push updates, change settings, or even reconfigure SSH parameters from a central dashboard, without needing direct physical access to the Raspberry Pi. This level of control is invaluable for large-scale IoT deployments where devices might be scattered across various geographical locations.Secure Authentication Methods
Security is paramount when dealing with remote access. The remote IoT platform emphasizes secure authentication, supporting both system user credentials and SSH key-based secure authentication. While password-based authentication is common, SSH key-based authentication offers a significantly higher level of security. It involves generating a pair of cryptographic keys: a public key that resides on your Raspberry Pi and a private key that you keep secure on your local machine. When you attempt to connect, the SSH client uses your private key to prove your identity to the Raspberry Pi, which verifies it against the public key. This method eliminates the risk of brute-force password attacks and provides a much more robust security posture. The platform ensures that there are "no security holes in other private client tools and protocols" by adhering to industry best practices and utilizing well-vetted open-source components. This commitment to security provides peace of mind, knowing that your remote connections are protected by strong cryptographic measures. For those looking to master remote control, file transfer, and secure internet access for their Pi projects, understanding and implementing these secure authentication methods is crucial.Enabling SSH on Your Raspberry Pi: A Step-by-Step Guide
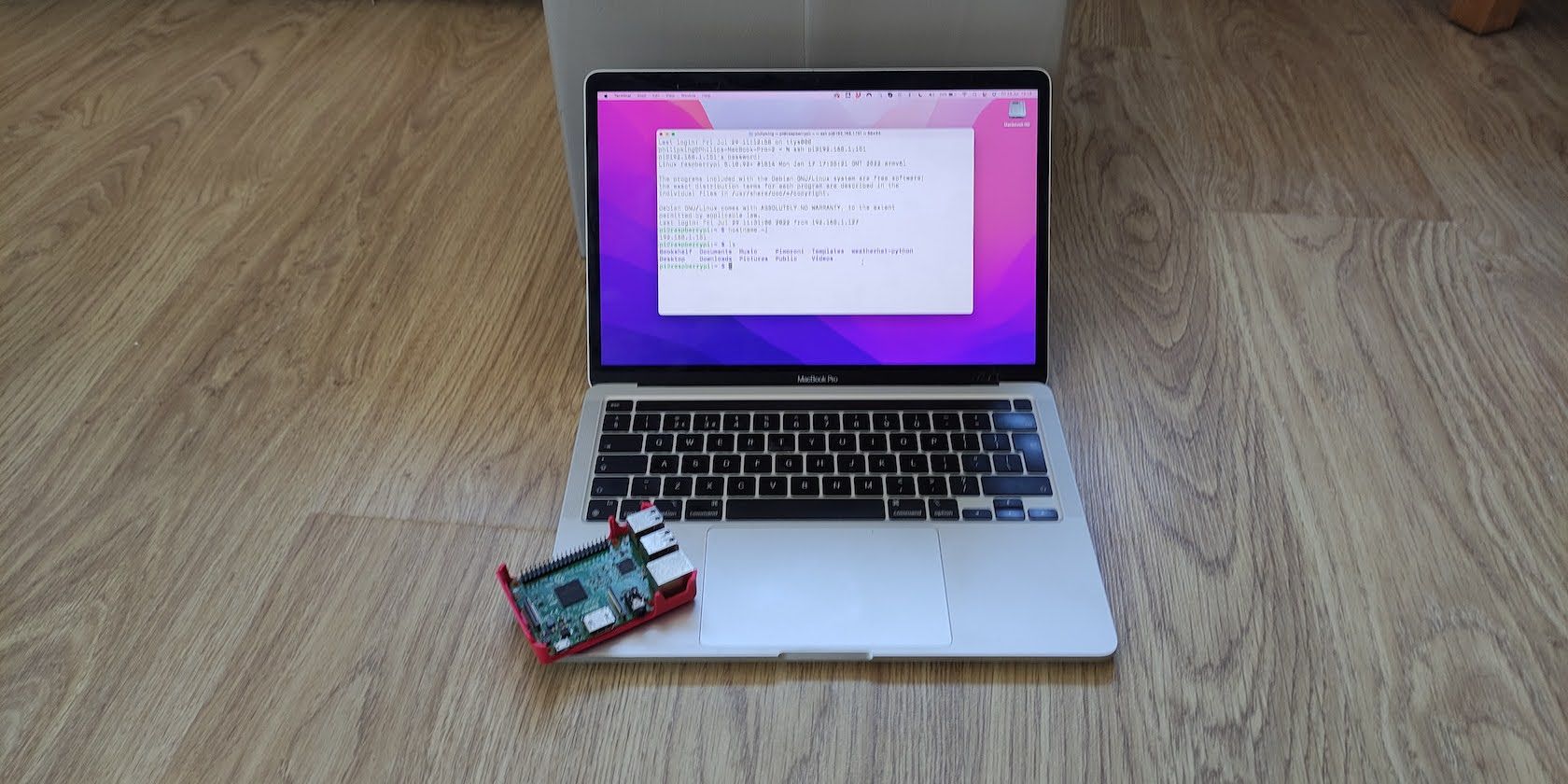
Enabling SSH on your Raspberry Pi is a straightforward process, but it requires attention to detail to ensure everything is configured correctly. This section will guide you through the initial steps, whether you're setting up a new Pi or configuring an existing one for remote IoT platform integration. The goal is to get your Raspberry Pi ready to communicate securely with the remote IoT platform, unlocking its full potential for remote management.Initial Setup and Network Access
Before you can connect your Raspberry Pi to a remote IoT platform, you need to ensure SSH is enabled and your Pi has network access. For new Raspberry Pi OS installations, SSH is often disabled by default for security reasons. You can enable it in several ways:- Via Raspberry Pi Configuration Tool (Desktop Environment): If you have a monitor and keyboard connected, go to `Menu > Preferences > Raspberry Pi Configuration > Interfaces` tab and enable SSH.
- Via `raspi-config` (Terminal): From the terminal, type `sudo raspi-config`, navigate to `Interface Options`, then `SSH`, and select `Yes`.
- Headless Setup (Before First Boot): If you're setting up a headless Pi, you can enable SSH by creating an empty file named `ssh` (no extension) in the boot partition of your SD card. When the Pi boots, it will detect this file and enable SSH.
Connecting to the RemoteIoT Portal
After you've gained local SSH access to your Raspberry Pi, the next step is to install the remote IoT service. This service acts as a bridge, allowing your Pi to securely connect to the remote IoT platform's dashboard. The exact steps for installing the service will depend on the specific remote IoT platform you choose, but typically it involves running a few commands in your Raspberry Pi's terminal.- Install the RemoteIoT Service: Open the terminal of your Raspberry Pi (either directly or via SSH on the local network) and install the remote IoT service. This usually involves a `curl` command followed by `bash` to execute a setup script provided by the platform.
- Connect Your Raspberry Pi: Once the service is installed and running, open the remote IoT portal in your browser and log in to the dashboard.
- Verify Device Connection: You should now see your Raspberry Pi listed in the list of account devices. This indicates a successful connection, and your Pi is now ready for remote management through the platform.
Mastering Remote Control and File Transfer
With SSH enabled and your Raspberry Pi connected to a remote IoT platform, you unlock a world of possibilities for remote control and file transfer. This is where the true power of "ssh remoteiot raspberry pi" becomes evident. You can execute commands on your Pi from anywhere in the world, allowing you to restart services, update software, run diagnostic checks, or even trigger specific actions on connected hardware. For example, you could remotely toggle a relay connected to your Pi to turn lights on or off, or retrieve sensor data logs with a simple command. File transfer is equally critical. Whether you need to upload new scripts, download collected sensor data, or back up important configuration files, SSH provides secure methods. Tools like `scp` (Secure Copy Protocol) or `sftp` (SSH File Transfer Protocol) allow you to move files between your local machine and your Raspberry Pi securely. Many remote IoT platforms integrate these functionalities into their web interface, simplifying the process even further. This means you can download Raspberry Pi configurations, update firmware, or deploy new applications with just a few clicks from your browser, without needing to learn complex command-line tools. Mastering these capabilities is essential for efficient IoT device management.Enhancing Security: Avoiding Pitfalls and Best Practices
While SSH provides a secure channel, neglecting best practices can introduce vulnerabilities. The phrase "no security holes in other private client tools and protocols" highlights the importance of using reputable software and following secure configurations. Here are key considerations for enhancing the security of your "ssh remoteiot raspberry pi" setup:- Use SSH Key-Based Authentication: As mentioned, this is far more secure than passwords. Disable password authentication for SSH once keys are set up.
- Strong Passwords for System Users: If you must use passwords, ensure they are long, complex, and unique.
- Change Default Username: Avoid using the default `pi` username. Create a new user with `sudo` privileges and disable or delete the `pi` user.
- Change Default SSH Port: The default SSH port is 22. Changing it to a non-standard port (e.g., 2222) can deter automated scanning bots, though it's not a security measure on its own.
- Firewall Configuration: Implement a firewall (like `ufw` on Linux) on your Raspberry Pi to restrict incoming connections to only necessary ports and trusted IP addresses.
- Regular Updates: Keep your Raspberry Pi's operating system and all installed software up to date. This ensures you have the latest security patches.
- Limit Access: Grant SSH access only to users who absolutely need it. Use `sudo` for administrative tasks rather than logging in as root directly.
- Monitor Logs: Regularly check SSH logs for unusual activity or failed login attempts.
- VPN for Extra Layer: For highly sensitive applications, consider routing your SSH traffic through a VPN for an additional layer of encryption and anonymity.
Revolutionizing IoT Projects with RemoteIoT Monitoring
Beyond just control and file transfer, a key aspect of any robust IoT deployment is monitoring. The "remoteiot monitoring ssh download raspberry pi" capability transforms how you oversee your devices. This guide will provide you with a detailed overview of how to set up, configure, and troubleshoot remote IoT monitoring using SSH on Raspberry Pi. Imagine being able to check the CPU usage, memory consumption, disk space, or even the status of specific applications running on your remote Raspberry Pi, all from a centralized dashboard. This real-time visibility is crucial for proactive maintenance, identifying potential issues before they escalate, and ensuring the continuous operation of your IoT ecosystem. Remote IoT platforms often integrate monitoring agents that collect data from your Raspberry Pi and transmit it securely back to the dashboard. This data can then be visualized through graphs, alerts, and custom dashboards, providing actionable insights into the health and performance of your devices. For example, if a sensor stops transmitting data, the monitoring system can immediately alert you, allowing for swift troubleshooting via SSH. This proactive approach minimizes downtime and maximizes the efficiency of your IoT solutions. Discover the best IoT device remote SSH Raspberry Pi free options with this comprehensive guide, which covers setup, security, and troubleshooting tips for remote monitoring.Overcoming NAT and Firewall Challenges with Secure Tunnels
One of the most common hurdles in remote IoT device management is dealing with Network Address Translation (NAT) and firewalls. Most IoT devices, including Raspberry Pis, are typically located behind a NAT router or a corporate firewall, making them inaccessible directly from the internet. This is where solutions like the SocketXP IoT platform become invaluable. SocketXP IoT platform provides remote SSH access to IoT devices behind NAT router or firewall over the internet using secure SSL/TLS VPN tunnels. This creates a secure, persistent connection from your Raspberry Pi to the platform's cloud infrastructure, effectively bypassing the limitations of NAT and firewalls. This tunneling technology means you don't need to configure port forwarding on your router or request static IP addresses, which can be complex or even impossible in many scenarios. The secure tunnel acts as a bridge, allowing you to initiate an SSH connection to your Raspberry Pi as if it had a public IP address, all while maintaining a high level of security through SSL/TLS encryption. This capability is particularly beneficial for developers and hobbyists who need to access their devices from various locations without compromising network security. In this article, we will explore the key components of a remote IoT system, including the role of VPC (Virtual Private Cloud) in creating a secure network, the importance of SSH for secure access, and how tunneling solutions facilitate connectivity.Conclusion: Mastering SSH RemoteIoT Raspberry Pi
In conclusion, "ssh remoteiot raspberry pi" is a powerful combination that enables secure and efficient remote access to your IoT projects. From setting up SSH on your Raspberry Pi to leveraging advanced remote IoT platforms for seamless management and monitoring, the capabilities are vast. This comprehensive guide has aimed to shed light on how to take full control of your Raspberry Pi with remote SSH access, covering everything from initial setup and secure authentication to advanced monitoring and overcoming network challenges. Whether you're a developer, hobbyist, or system administrator, understanding how to set up and use web SSH can significantly enhance your productivity and the reliability of your IoT deployments. The free download concept associated with "ssh remoteiot raspberry pi" makes these powerful tools accessible to everyone, fostering innovation and expanding the reach of IoT. Mastering "remoteiot vpc ssh on raspberry pi" and understanding how to download configurations securely can significantly enhance your IoT capabilities, providing a robust foundation for any project. We encourage you to experiment with these technologies, apply the best practices outlined, and share your experiences. What remote IoT projects are you planning to unlock with SSH and your Raspberry Pi? Share your thoughts in the comments below!- Mark Singer Gorilla Glue Passed Away
- Naked Priyanka Chopra
- Pat Monahan Wife
- Ipcam Guys Telegram
- Frankie Faison
How to SSH Into a Raspberry Pi for Remote Access

Raspberry Pi: How to enable SSH

How to SSH Into a Raspberry Pi for Remote Access